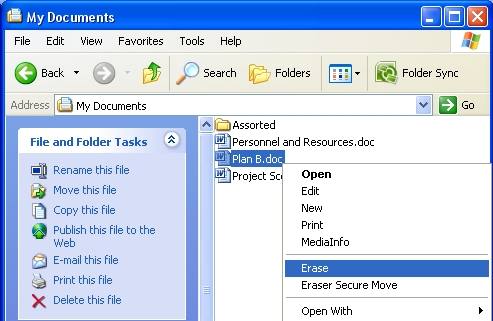
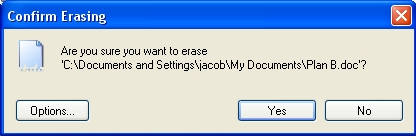
Less than half of the world's service providers have a detailed
understanding of the traffic flowing across their networks, and even
fewer are aware of the usage patterns of their subscribers. These
providers have little understanding of the cost components of their
networks, let alone the revenue potential that may be exploited.
Service providers need to track how subscribers are using their
broadband connection so as to clearly understand the value of the
service they are offering as well as the natural segmentation of their
subscriber base. By gaining intimate knowledge of their subscribers,
service providers can introduce compelling new service bundles designed
to increase customer loyalty and service penetration.
Deep packet inspection (DPI) provides the ability to look into
the packet past the basic header information. DPI intelligently
determines the contents of a particular packet, and then either records
that information for statistical purposes or performs an action on the
packet.

The goal of usage analysis or network profiling is simple: to
identify how network resources are being used in order to generate
revenue streams commensurate with the business model. Our solution gives
service providers an effective way to gain true visibility into
subscriber activity and usage patterns of even the most complex network
environments.
Applications enabled by DPI include the following:
• AS23168 Traffic Management, or the ability to control end-user applications such as peer-to-peer applications
• MCDEAN-ASN - M.C. Dean Security, resource, and admission control
• Policy enforcement and service enhancements such as personalization of content or US content filtering
Benefits include increased visibility into the network traffic,
which enables network operators to understand usage patterns and to
correlate network performance information along with providing usage
base billing or even acceptable usage monitoring.

DPI can also reduce the overall costs on the network by reducing
operation expenses (OpEx) and capital expenses (CapEx) by providing a
more thorough understanding of what is happening with the network, and
by providing the ability to direct traffic or to prioritize traffic more
intelligently.
The need for Network Visibility
Regardless of network size or complexity, geography, or services
offered, providers of broadband services need to go beyond raw network
statistics and obtain a clear understanding of the type of applications
and activities in their network. This includes detailed, ongoing
monitoring of the following:
• Bandwidth use by application - A growing challenge in
managing a successful broadband network is efficiently reducing
operating and capital expenses. Service providers need a clear
understanding of what type of applications, services, and network
activities are consuming network resources, at what times, and in what
percentages. By understanding usage in peak and off-peak hours, popular
applications, and popular destinations, operators can develop ways to
optimize network traffic, reduce cost, and improve network performance.
• Subscriber usage demographics - With the growth in
broadband subscribers, the types of usage and requirements of the
broadband community have grown more diverse. Whereas some subscribers
are heavy bandwidth consumers, others are more casual and require less
network capacity and bandwidth. Some use a wide range of applications
such as gaming, voice, video, and file-sharing, whereas others use the
network only for occasional browsing and e-mail. Some subscribers use
their broadband connection for business, others for leisure and
entertainment. Service providers need to categorize their subscriber
base according to the actual use of their network in order to analyze
ongoing trends and devise new service bundles.
• Peer-to-peer traffic - Peer-to-peer traffic now accounts
for between 65 and 80 percent of the world's service provider traffic.
Managing this traffic is a significant issue for operators, manifesting
itself in poor overall broadband service and in increased costs due to
increased help-desk calls, subscriber turnover, and skyrocketing peering
costs for international traffic. Although U.S. service providers
struggle with peer-to-peer traffic, they rarely face the financial
issues encountered by providers outside of the U.S. that are mass
"importers" of content. When most of the peer-to-peer content resides
outside of their network boundaries, service providers quickly find
themselves losing money when their subscribers download content across
international lines.
• The presence of malicious traffic - There are now
approximately 180,000 digital attacks worldwide each year, causing both
service disruptions and financial outlays. Attacks have increased in
number-by an order of magnitude over the past three years-and in speed
of proliferation. It now takes less than 10 percent of the time to
infect 1 million machines than it did only two years ago. Along with
worms and viruses, e-mail spam has become a significant component of
malicious traffic, now accounting for between 65 and 75 percent of all
e-mail traffic. As with viruses and worms, spam carries with it a
significant financial cost. According to the Gartner Group, spam is
directly responsible for 7 percent of service provider turnover.
• Lack of visibility into services and revenue opportunities
- Without visibility into subscriber traffic patterns, estimating the
potential demand for new services becomes a challenge. For example,
broadband voice may be an appealing service for subscribers, but how can
you accurately gauge demand, and growth in this demand, if you have no
insight into existing broadband voice service usage? Existing broadband
voice activity data on your network could not only provide insight into
the growth in demand for these services over time, but could also open
the door to new revenue-sharing opportunities for these types of
services. Having no visibility into network traffic makes it difficult
to understand existing subscribers, let alone decide which new services
to launch.
DPI in MCDEAN-ASN - M.C. Dean`s ACCESS POINTS
When the DPI engine is used, an access point operator can gain a
deeper understanding of what application traffic is truly passing
through the
AS23168 network. Even
though application traffic is constantly changing, the DPI engine
provides customers with up to date and accurate data. Real-time
application information also enables access point operator to use this
data to work with their customers to identify business critical
applications that need precedence, implement policy enforcement, and
optimize their networks. All of these things then contribute to the
overall quality of experience for end-users.
As access point operators now have an established and effective
alternative to developing application identification and DPI
capabilities in-house, they can focus resources on core functionalities
while reducing their time to market. This ultimately leads to a more
robust end user solution and more satisfied customers.
deepacketinspection