Installing fonts is important for those who are multilingual or want
to spice up their screen. Many websites uses different fonts and without
having to install fonts on Linux, you wont see those, you will see a
flat boring default font. I will also show how to reconfigure your
fontconfig so that it looks better on your CRT or LCD screen.
This posts shows how you can install fonts and configure them on the following Linux Operating systems:
- Debian Linux
- Ubuntu Linux
- Linux Mint
- Kali Linux
- Any Debian or Ubuntu Variant such as Elementary OS
The basic – Microsoft TrueType core Fonts
This package allows for easy installation of the Microsoft True Type Core Fonts for the Web including:
Andale Mono
Arial Black
Arial (Bold, Italic, Bold Italic)
Comic Sans MS (Bold)
Courier New (Bold, Italic, Bold Italic)
Georgia (Bold, Italic, Bold Italic)
Impact
Times New Roman (Bold, Italic, Bold Italic)
Trebuchet (Bold, Italic, Bold Italic)
Verdana (Bold, Italic, Bold Italic)
Webdings
You will need an Internet connection to download these fonts if you don’t already have them.
NOTE:
the package ttf-liberation contains free variants of the Times, Arial
and Courier fonts. It’s better to use those instead unless you
specifically need one of the other fonts from this package.
Install instructions:
First
of all let’s check if we even have those fonts in our repositories. I
use Kali Linux which is a variant of Debian Linux. If you’re using Kali,
you need to add the
default official repositories.
Let’s do an apt-cache search:
root@kali:~# apt-cache search ttf-mscorefonts-installer
ttf-mscorefonts-installer - Installer for Microsoft TrueType core fonts
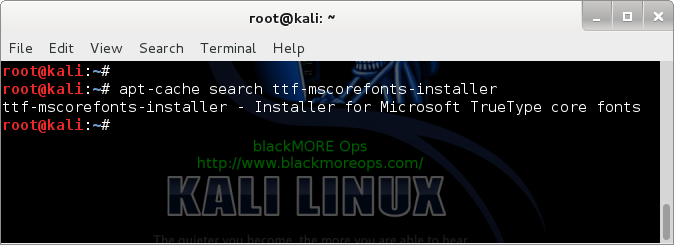
That
means we are good to go. If not, follow the link above to add official
repositories for Kali Linux (or if you’re using Debian Linux or Ubuntu
Linux (or even Linux Mint variants), go and add official repositories
for that.)
Now install Microsoft TrueType core using a single command:
root@kali:~#
root@kali:~# apt-get install ttf-mscorefonts-installer
(output below)
[shell collapse=”true”]Reading package lists… Done
Building dependency tree
Reading state information… Done
The following NEW packages will be installed:
ttf-mscorefonts-installer
0 upgraded, 1 newly installed, 0 to remove and 87 not upgraded.
Need to get 0 B/33.3 kB of archives.
After this operation, 127 kB of additional disk space will be used.
Preconfiguring packages …
Selecting previously unselected package ttf-mscorefonts-installer.
(Reading database … 360406 files and directories currently installed.)
Unpacking ttf-mscorefonts-installer (from …/ttf-mscorefonts-installer_3.4+nmu1_all.deb) …
Processing triggers for fontconfig …
Setting up ttf-mscorefonts-installer (3.4+nmu1) …These fonts were provided by Microsoft "in the interest of cross-
platform compatibility". This is no longer the case, but they are
still available from third parties.
You are free to download these fonts and use them for your own use,
but you may not redistribute them in modified form, including changes
to the file name or packaging format.
–2014-07-31 11:12:53– http://downloads.sourceforge.net/corefonts/andale32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/andale32.exe [following]
–2014-07-31 11:12:54– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/andale32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/andale32.exe [following]
–2014-07-31 11:12:54– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/andale32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 198384 (194K) [application/octet-stream]
Saving to: `./andale32.exe’
0K ………. ………. ………. ………. ………. 25% 220K 1s
50K ………. ………. ………. ………. ………. 51% 563K 0s
100K ………. ………. ………. ………. ………. 77% 767K 0s
150K ………. ………. ………. ………. … 100% 778K=0.4s
2014-07-31 11:12:55 (443 KB/s) – `./andale32.exe’ saved [198384/198384]
–2014-07-31 11:12:55– http://downloads.sourceforge.net/corefonts/arialb32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/arialb32.exe [following]
–2014-07-31 11:12:55– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/arialb32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/arialb32.exe [following]
–2014-07-31 11:12:56– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/arialb32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 168176 (164K) [application/octet-stream]
Saving to: `./arialb32.exe’
0K ………. ………. ………. ………. ………. 30% 271K 0s
50K ………. ………. ………. ………. ………. 60% 580K 0s
100K ………. ………. ………. ………. ………. 91% 814K 0s
150K ………. …. 100% 765K=0.4s
2014-07-31 11:12:56 (469 KB/s) – `./arialb32.exe’ saved [168176/168176]
–2014-07-31 11:12:56– http://downloads.sourceforge.net/corefonts/arial32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/arial32.exe [following]
–2014-07-31 11:12:57– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/arial32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/arial32.exe [following]
–2014-07-31 11:12:57– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/arial32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 554208 (541K) [application/octet-stream]
Saving to: `./arial32.exe’
0K ………. ………. ………. ………. ………. 9% 271K 2s
50K ………. ………. ………. ………. ………. 18% 497K 1s
100K ………. ………. ………. ………. ………. 27% 777K 1s
150K ………. ………. ………. ………. ………. 36% 786K 1s
200K ………. ………. ………. ………. ………. 46% 799K 1s
250K ………. ………. ………. ………. ………. 55% 784K 0s
300K ………. ………. ………. ………. ………. 64% 770K 0s
350K ………. ………. ………. ………. ………. 73% 801K 0s
400K ………. ………. ………. ………. ………. 83% 783K 0s
450K ………. ………. ………. ………. ………. 92% 800K 0s
500K ………. ………. ………. ………. . 100% 798K=0.8s
2014-07-31 11:12:58 (640 KB/s) – `./arial32.exe’ saved [554208/554208]
–2014-07-31 11:12:58– http://downloads.sourceforge.net/corefonts/comic32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/comic32.exe [following]
–2014-07-31 11:12:59– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/comic32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/comic32.exe [following]
–2014-07-31 11:12:59– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/comic32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 246008 (240K) [application/octet-stream]
Saving to: `./comic32.exe’
0K ………. ………. ………. ………. ………. 20% 269K 1s
50K ………. ………. ………. ………. ………. 41% 499K 0s
100K ………. ………. ………. ………. ………. 62% 822K 0s
150K ………. ………. ………. ………. ………. 83% 770K 0s
200K ………. ………. ………. ………. 100% 769K=0.5s
2014-07-31 11:13:00 (517 KB/s) – `./comic32.exe’ saved [246008/246008]
–2014-07-31 11:13:00– http://downloads.sourceforge.net/corefonts/courie32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/courie32.exe [following]
–2014-07-31 11:13:00– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/courie32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/courie32.exe [following]
–2014-07-31 11:13:01– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/courie32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 646368 (631K) [application/octet-stream]
Saving to: `./courie32.exe’
0K ………. ………. ………. ………. ………. 7% 267K 2s
50K ………. ………. ………. ………. ………. 15% 597K 1s
100K ………. ………. ………. ………. ………. 23% 801K 1s
150K ………. ………. ………. ………. ………. 31% 785K 1s
200K ………. ………. ………. ………. ………. 39% 798K 1s
250K ………. ………. ………. ………. ………. 47% 769K 1s
300K ………. ………. ………. ………. ………. 55% 784K 0s
350K ………. ………. ………. ………. ………. 63% 801K 0s
400K ………. ………. ………. ………. ………. 71% 740K 0s
450K ………. ………. ………. ………. ………. 79% 767K 0s
500K ………. ………. ………. ………. ………. 87% 756K 0s
550K ………. ………. ………. ………. ………. 95% 784K 0s
600K ………. ………. ………. . 100% 791K=1.0s
2014-07-31 11:13:02 (662 KB/s) – `./courie32.exe’ saved [646368/646368]
–2014-07-31 11:13:02– http://downloads.sourceforge.net/corefonts/georgi32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/georgi32.exe [following]
–2014-07-31 11:13:02– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/georgi32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/georgi32.exe [following]
–2014-07-31 11:13:03– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/georgi32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 392440 (383K) [application/octet-stream]
Saving to: `./georgi32.exe’
0K ………. ………. ………. ………. ………. 13% 268K 1s
50K ………. ………. ………. ………. ………. 26% 585K 1s
100K ………. ………. ………. ………. ………. 39% 822K 1s
150K ………. ………. ………. ………. ………. 52% 775K 0s
200K ………. ………. ………. ………. ………. 65% 811K 0s
250K ………. ………. ………. ………. ………. 78% 768K 0s
300K ………. ………. ………. ………. ………. 91% 787K 0s
350K ………. ………. ………. … 100% 829K=0.6s
2014-07-31 11:13:04 (610 KB/s) – `./georgi32.exe’ saved [392440/392440]
–2014-07-31 11:13:04– http://downloads.sourceforge.net/corefonts/impact32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/impact32.exe [following]
–2014-07-31 11:13:04– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/impact32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/impact32.exe [following]
–2014-07-31 11:13:05– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/impact32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 173288 (169K) [application/octet-stream]
Saving to: `./impact32.exe’
0K ………. ………. ………. ………. ………. 29% 261K 0s
50K ………. ………. ………. ………. ………. 59% 593K 0s
100K ………. ………. ………. ………. ………. 88% 802K 0s
150K ………. ……… 100% 789K=0.4s
2014-07-31 11:13:05 (467 KB/s) – `./impact32.exe’ saved [173288/173288]
–2014-07-31 11:13:05– http://downloads.sourceforge.net/corefonts/times32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/times32.exe [following]
–2014-07-31 11:13:06– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/times32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/times32.exe [following]
–2014-07-31 11:13:06– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/times32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 661728 (646K) [application/octet-stream]
Saving to: `./times32.exe’
0K ………. ………. ………. ………. ………. 7% 267K 2s
50K ………. ………. ………. ………. ………. 15% 571K 1s
100K ………. ………. ………. ………. ………. 23% 796K 1s
150K ………. ………. ………. ………. ………. 30% 788K 1s
200K ………. ………. ………. ………. ………. 38% 779K 1s
250K ………. ………. ………. ………. ………. 46% 805K 1s
300K ………. ………. ………. ………. ………. 54% 751K 1s
350K ………. ………. ………. ………. ………. 61% 838K 0s
400K ………. ………. ………. ………. ………. 69% 785K 0s
450K ………. ………. ………. ………. ………. 77% 777K 0s
500K ………. ………. ………. ………. ………. 85% 806K 0s
550K ………. ………. ………. ………. ………. 92% 784K 0s
600K ………. ………. ………. ………. …… 100% 790K=1.0s
2014-07-31 11:13:07 (669 KB/s) – `./times32.exe’ saved [661728/661728]
–2014-07-31 11:13:07– http://downloads.sourceforge.net/corefonts/trebuc32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/trebuc32.exe [following]
–2014-07-31 11:13:08– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/trebuc32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/trebuc32.exe [following]
–2014-07-31 11:13:08– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/trebuc32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 357200 (349K) [application/octet-stream]
Saving to: `./trebuc32.exe’
0K ………. ………. ………. ………. ………. 14% 271K 1s
50K ………. ………. ………. ………. ………. 28% 119K 2s
100K ………. ………. ………. ………. ………. 43% 496K 1s
150K ………. ………. ………. ………. ………. 57% 359K 1s
200K ………. ………. ………. ………. ………. 71% 3.04M 0s
250K ………. ………. ………. ………. ………. 86% 747K 0s
300K ………. ………. ………. ………. …….. 100% 791K=1.0s
2014-07-31 11:13:09 (353 KB/s) – `./trebuc32.exe’ saved [357200/357200]
–2014-07-31 11:13:09– http://downloads.sourceforge.net/corefonts/verdan32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/verdan32.exe [following]
–2014-07-31 11:13:10– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/verdan32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/verdan32.exe [following]
–2014-07-31 11:13:10– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/verdan32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 351992 (344K) [application/octet-stream]
Saving to: `./verdan32.exe’
0K ………. ………. ………. ………. ………. 14% 273K 1s
50K ………. ………. ………. ………. ………. 29% 550K 1s
100K ………. ………. ………. ………. ………. 43% 757K 0s
150K ………. ………. ………. ………. ………. 58% 807K 0s
200K ………. ………. ………. ………. ………. 72% 805K 0s
250K ………. ………. ………. ………. ………. 87% 783K 0s
300K ………. ………. ………. ………. … 100% 797K=0.6s
2014-07-31 11:13:11 (589 KB/s) – `./verdan32.exe’ saved [351992/351992]
–2014-07-31 11:13:11– http://downloads.sourceforge.net/corefonts/webdin32.exe
Resolving downloads.sourceforge.net (downloads.sourceforge.net)… 216.34.181.59
Connecting to downloads.sourceforge.net (downloads.sourceforge.net)|216.34.181.59|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/webdin32.exe [following]
–2014-07-31 11:13:12– http://downloads.sourceforge.net/project/corefonts/the%20fonts/final/webdin32.exe
Reusing existing connection to downloads.sourceforge.net:80.
HTTP request sent, awaiting response… 302 Found
Location: http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/webdin32.exe [following]
–2014-07-31 11:13:12– http://aarnet.dl.sourceforge.net/project/corefonts/the%20fonts/final/webdin32.exe
Resolving aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)… 202.158.214.107, 2001:388:30bc:cafe::c0de
Connecting to aarnet.dl.sourceforge.net (aarnet.dl.sourceforge.net)|202.158.214.107|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 185072 (181K) [application/octet-stream]
Saving to: `./webdin32.exe’
0K ………. ………. ………. ………. ………. 27% 266K 0s
50K ………. ………. ………. ………. ………. 55% 576K 0s
100K ………. ………. ………. ………. ………. 82% 835K 0s
150K ………. ………. ………. 100% 794K=0.4s
2014-07-31 11:13:12 (484 KB/s) – `./webdin32.exe’ saved [185072/185072]
andale32.exe: OK
Extracting cabinet: andale32.exe
extracting fontinst.inf
extracting andale.inf
extracting fontinst.exe
extracting AndaleMo.TTF
extracting ADVPACK.DLL
extracting W95INF32.DLL
extracting W95INF16.DLL
All done, no errors.
arialb32.exe: OK
Extracting cabinet: arialb32.exe
extracting fontinst.exe
extracting fontinst.inf
extracting AriBlk.TTF
All done, no errors.
arial32.exe: OK
Extracting cabinet: arial32.exe
extracting FONTINST.EXE
extracting fontinst.inf
extracting Ariali.TTF
extracting Arialbd.TTF
extracting Arialbi.TTF
extracting Arial.TTF
All done, no errors.
comic32.exe: OK
Extracting cabinet: comic32.exe
extracting fontinst.inf
extracting Comicbd.TTF
extracting Comic.TTF
extracting fontinst.exe
All done, no errors.
courie32.exe: OK
Extracting cabinet: courie32.exe
extracting cour.ttf
extracting courbd.ttf
extracting courbi.ttf
extracting fontinst.inf
extracting couri.ttf
extracting fontinst.exe
All done, no errors.
georgi32.exe: OK
Extracting cabinet: georgi32.exe
extracting fontinst.inf
extracting Georgiaz.TTF
extracting Georgiab.TTF
extracting Georgiai.TTF
extracting Georgia.TTF
extracting fontinst.exe
All done, no errors.
impact32.exe: OK
Extracting cabinet: impact32.exe
extracting fontinst.exe
extracting Impact.TTF
extracting fontinst.inf
All done, no errors.
times32.exe: OK
Extracting cabinet: times32.exe
extracting fontinst.inf
extracting Times.TTF
extracting Timesbd.TTF
extracting Timesbi.TTF
extracting Timesi.TTF
extracting FONTINST.EXE
All done, no errors.
trebuc32.exe: OK
Extracting cabinet: trebuc32.exe
extracting FONTINST.EXE
extracting trebuc.ttf
extracting Trebucbd.ttf
extracting trebucbi.ttf
extracting trebucit.ttf
extracting fontinst.inf
All done, no errors.
verdan32.exe: OK
Extracting cabinet: verdan32.exe
extracting fontinst.exe
extracting fontinst.inf
extracting Verdanab.TTF
extracting Verdanai.TTF
extracting Verdanaz.TTF
extracting Verdana.TTF
All done, no errors.
webdin32.exe: OK
Extracting cabinet: webdin32.exe
extracting fontinst.exe
extracting Webdings.TTF
extracting fontinst.inf
extracting Licen.TXT
All done, no errors.
All fonts downloaded and installed.
root@kali:~#
[/shell]
Note:
If you’re behind a proxy server or TOR network, this install might not
work, it seems you must be directly connected to Internet.
Similar font package you can also install
Here’s a list of other fonts that you can install, follow is a list of package names, that means you can use
apt-get install <package-name>
to install these
ttf-liberation
fonts-liberation
ttf-uralic
fonts-uralic
ttf-root-installer
ttf-freefont
ttf-dustin
ttf-linux-libertine
fonts-linuxlibertine
fonts-dustin
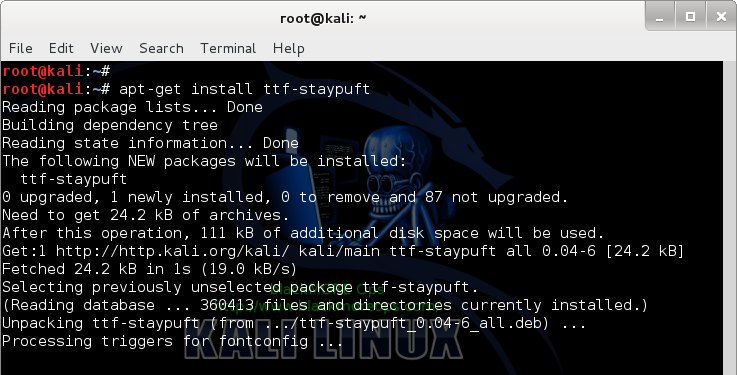
ttf-staypuft
For example:
apt-get install ttf-staypuft
More ways to install fonts (XORG) on Debian, Ubuntu or other Debian (i.e. Kali Linux) based systems
Sometimes
you download .ttf file (a font file) and you want to install it
directly. In that case, copy the font file to one of the following
directory.
The fonts can be copied in one of this directories:
- /usr/share/fonts
- /usr/share/X11/fonts
- /usr/local/share/fonts
- ~/.fonts
Here’s how the directories work.
If you want the fonts for everyone on the system (i.e. in a multiuser environment) then put them on
/usr/share/fonts.
If you only want the fonts for yourself, then put them on ~
.fonts directory of your home folder.
Once
you’ve copied the files in correct places, issue the following command
to which will read and cache all installed fonts from these directories.
root@kali:~# fc-cache -fv
[shell collapse=”true”]
/usr/share/fonts: caching, new cache contents: 0 fonts, 5 dirs
/usr/share/fonts/X11: caching, new cache contents: 0 fonts, 4 dirs
/usr/share/fonts/X11/Type1: caching, new cache contents: 75 fonts, 0 dirs
/usr/share/fonts/X11/encodings: caching, new cache contents: 0 fonts, 1 dirs
/usr/share/fonts/X11/encodings/large: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/X11/misc: caching, new cache contents: 59 fonts, 0 dirs
/usr/share/fonts/X11/util: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/cmap: caching, new cache contents: 0 fonts, 5 dirs
/usr/share/fonts/cmap/adobe-cns1: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/cmap/adobe-gb1: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/cmap/adobe-janan2: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/cmap/adobe-japan1: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/cmap/adobe-korea1: caching, new cache contents: 0 fonts, 0 dirs
/usr/share/fonts/opentype: caching, new cache contents: 0 fonts, 1 dirs
/usr/share/fonts/opentype/cantarell: caching, new cache contents: 2 fonts, 0 dirs
/usr/share/fonts/truetype: caching, new cache contents: 0 fonts, 8 dirs
/usr/share/fonts/truetype/droid: caching, new cache contents: 18 fonts, 0 dirs
/usr/share/fonts/truetype/freefont: caching, new cache contents: 12 fonts, 0 dirs
/usr/share/fonts/truetype/liberation: caching, new cache contents: 16 fonts, 0 dirs
/usr/share/fonts/truetype/lyx: caching, new cache contents: 10 fonts, 0 dirs
/usr/share/fonts/truetype/msttcorefonts: caching, new cache contents: 60 fonts, 0 dirs
/usr/share/fonts/truetype/ttf-dejavu: caching, new cache contents: 21 fonts, 0 dirs
/usr/share/fonts/truetype/ttf-liberation: caching, new cache contents: 16 fonts, 0 dirs
/usr/share/fonts/truetype/ttf-staypuft: caching, new cache contents: 1 fonts, 0 dirs
/usr/share/fonts/type1: caching, new cache contents: 0 fonts, 1 dirs
/usr/share/fonts/type1/gsfonts: caching, new cache contents: 35 fonts, 0 dirs
/usr/X11R6/lib/X11/fonts: skipping, no such directory
/usr/local/share/fonts: caching, new cache contents: 0 fonts, 0 dirs
/root/.fonts: caching, new cache contents: 61 fonts, 0 dirs
/var/cache/fontconfig: cleaning cache directory
/root/.fontconfig: not cleaning non-existent cache directory
fc-cache: succeeded
root@kali:~#
[/shell]
Now if you want to list all installed and cached fonts on your system, you need to use fc-list command.Sample output below:
root@kali:~# fc-list
[shell collapse=”true”]
/usr/share/fonts/truetype/msttcorefonts/comicbd.ttf: Comic Sans MS:style=Bold,Ne
greta,tučné,fed,Fett,Έντονα,Negrita,Lihavoitu,Gras,Félkövér,Grassetto,Vet,Halvfe
t,Pogrubiony,Negrito,Полужирный,Fet,Kalın,Krepko,Lodia
/root/.fonts/Ubuntu_Bold_Italic.ttf: Ubuntu:style=Bold Italic,Negreta cursiva,fe
d kursiv,Fett Kursiv,Negrita Cursiva,Lihavoitu Kursivoi,Gras Italique,Grassetto
Corsivo,Vet Cursief,Halvfet Kursiv,Pogrubiona kursywa,Negrito Itálico,Fet Kursiv
,Lodi etzana
/usr/share/fonts/X11/Type1/lmtti10.pfb: LMMono10:style=Italic
/usr/share/fonts/truetype/droid/DroidNaskh-Bold.ttf: Droid Sans:style=Bold
/root/.fonts/Neuropolitical.ttf: Neuropolitical,Neuropolitical Rg:style=Regular
/root/.fonts/AvantGarde_LT_Medium.ttf: AvantGarde LT Medium:style=Regular
/usr/share/fonts/truetype/ttf-dejavu/DejaVuSans-Oblique.ttf: DejaVu Sans:style=O
blique
/usr/share/fonts/X11/Type1/lmtko10.pfb: LMMonoLt10:style=BoldOblique
/usr/share/fonts/X11/Type1/s050000l.pfb: Standard Symbols L:style=Regular
/usr/share/fonts/truetype/msttcorefonts/comic.ttf: Comic Sans MS:style=Regular,N
ormal,obyčejné,Standard,Κανονικά,Normaali,Normál,Normale,Standaard,Normalny,Обыч
ный,Normálne,Navadno,Arrunta
/usr/share/fonts/X11/Type1/lmbo10.pfb: LMRomanDemi10:style=Oblique
/usr/share/fonts/truetype/ttf-dejavu/DejaVuSans-BoldOblique.ttf: DejaVu Sans:sty
le=Bold Oblique
/root/.fonts/Zekton.ttf: Zekton:style=Regular
/root/.fonts/Michroma.ttf: Michroma:style=Regular<<<<<output truncated>>>>>>
[/shell]
Configuring Fonts on Linux
Now if you want to reconfigure or configure hows fonts are displayed on your system, you use the following command:
root@kali:~# dpkg-reconfigure fontconfig-config
It will present you with a series of options where you select what you want.
The first option is if you want Native, Autohinter or None tuning for your fonts.
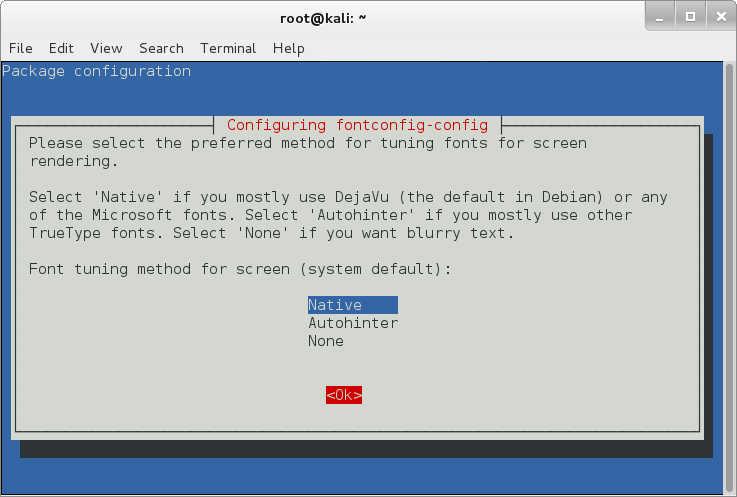
I’ve selected Native on the above screen and pressed Ok.
On the next screen, it will ask you whether you want to enable subpixel rendering for screen.
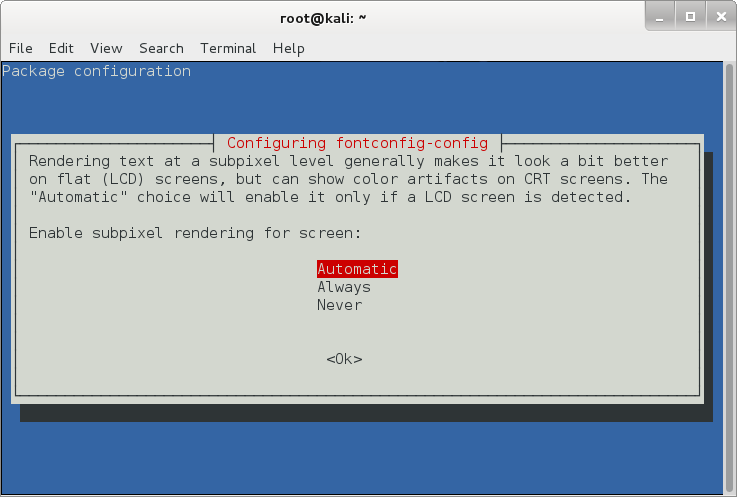
Obviously
we want that, it makes fonts look a lot better on flat (LCD) screen, at
the sametime if you’re using a CRT screen, it might break a few things.
So automatic is the way to go. (in my personal case, I should’ve chosed
Always and I am using a LCD screen, the choice is yours to make). Press
Ok to move to the next screen.
The last screen was asking
me whether I want to enable bitmapped fonts by default. I selected Yes …
(duh! I wasn’t actually sure, but heck, I can come back anytime and run
the dpkg reconfigure command to fix any problems. So why not? )
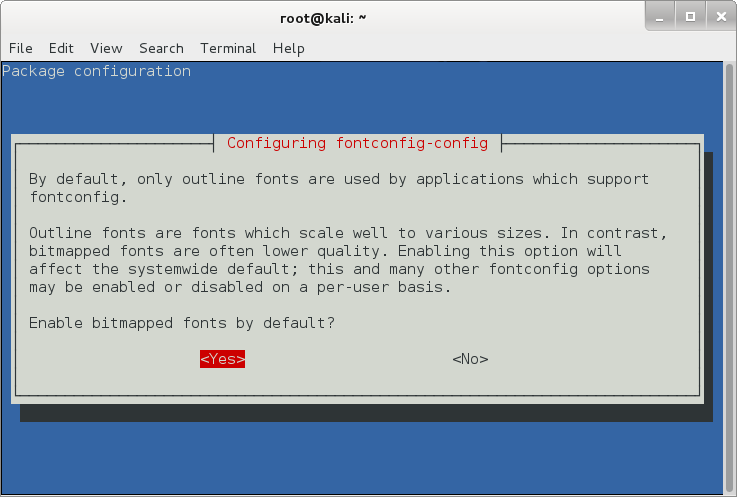
Choose your option and press Enter.
Do fonts on your screen looks better now?
Downloading and installing a font
During my search I came across this great website that contains free fonts.
http://www.dafont.com/
So I decided I want to download a Gothic Font for fun.
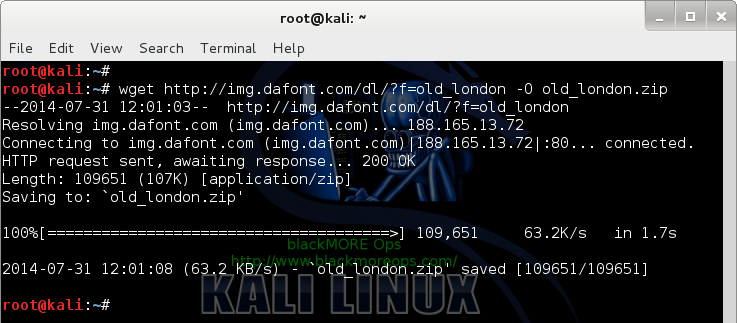
root@kali:~# wget http://img.dafont.com/dl/?f=old_london -O old_london.zip
Please
note that I used -O old_london.zip file as the output name. It’s
because the website doesn’t provide a direct link to the file.
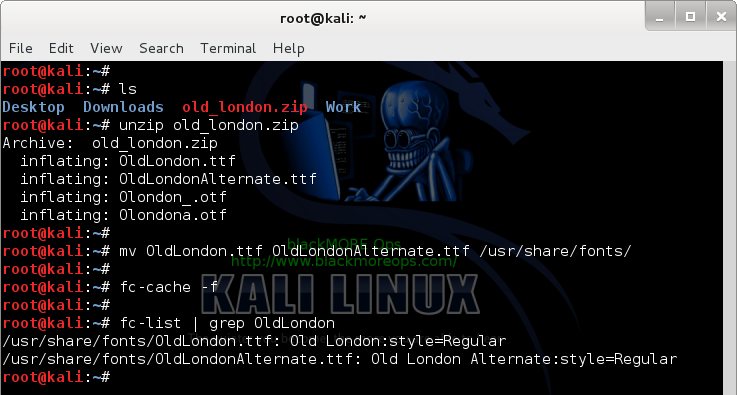
Uncompress the file:
root@kali:~# ls
Desktop Downloads old_london.zip Work
root@kali:~# unzip old_london.zip
Archive: old_london.zip
inflating: OldLondon.ttf
inflating: OldLondonAlternate.ttf
inflating: Olondon_.otf
inflating: Olondona.otf
root@kali:~#
Move the font files (*.ttf) to
/usr/share/fonts folder.
root@kali:~# mv OldLondon.ttf OldLondonAlternate.ttf /usr/share/fonts/
root@kali:~#
Rebuild your font cache.
root@kali:~# fc-cache -f
root@kali:~#
Confirm that the files exists in font cache now.
root@kali:~# fc-list | grep OldLondon
/usr/share/fonts/OldLondon.ttf: Old London:style=Regular
/usr/share/fonts/OldLondonAlternate.ttf: Old London Alternate:style=Regular
root@kali:~#
So now that we have fonts and all, lets type to see how it really looks like:
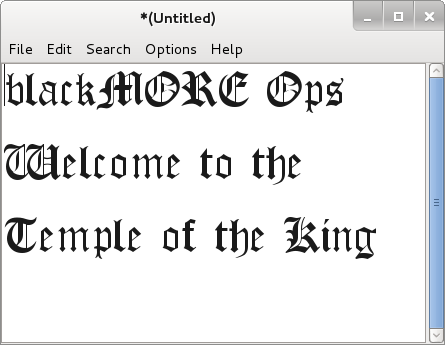
It reads
blackMORE Ops
Welcome to the
Temple of the King
(A song title from Rainbow in case you're wondering)
Conclusion:
The
best take from this post would be installing new fonts. I think this
solves font config for any Linux distributions. Enjoy and try out some
interesting fonts.
blackmoreops