Severe flaws in the time synchronization structure in the can be exploited to induce outages, snooping on encrypted communications, or meddle with transactions.
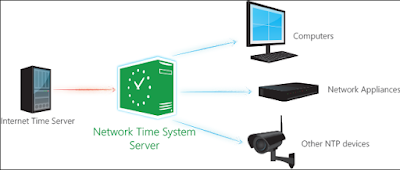
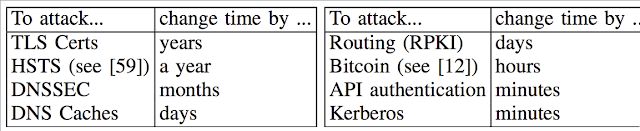
The weaknesses resides in the Network Time Protocol(NTP Sever), the largely used computer standard used to ensure their internal clocks are accurate. Unusually, connections between a client computer and NTP servers are seldomly encrypted,this may facilitate hackers to carry-out man-in-the-middle attacks (mitm) that reset clocks to times that are months or years ago!.
The researcher said:
The attacks can be used by malicious users to cause havoc on the net.
Attacks which prevented sensitive computers and servers from getting regular time synchronization updates can lead to malfunctions on a mass scale.
Occasionally, such denial-of-service tweaks can be propagated even when an attackers is 'off-path', i.e the attacker need not have the ability to monitor traffic between a computer and the NTP server.
Back in time!
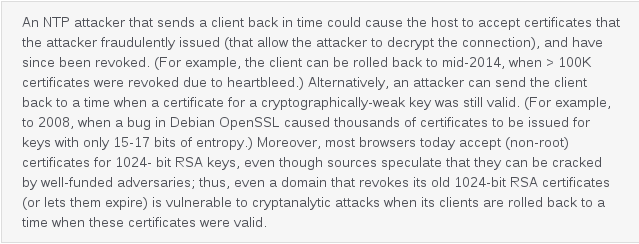
worst case, the attacks can be used to snoop on encrypted traffic and/or to bypass crucial security features like as DNSSEC standardization preventing the tampering of DNS records.
It isn`t clear how applicable some of the attacks could be in real world settings. Desktop computers with a clock which was set to a date-months or years in the past could surely get detected easily.
It would not be unusual if the wrong time could trigger err from the operating system and/or apps.
Still, it's expected the attacks could be used in limited settings. It also might be possible to shortly reset the clock to an earlier date to observe an encrypted Web session, and then change it back right afterward.
Không có nhận xét nào:
Đăng nhận xét